Python Code Execution + Cloud Misconfiguration: How a Simple Feature Exposed Sensitive Data

As companies rush to enhance their cloud-based analytics platforms with advanced features, even well-intentioned design choices can create dangerous blind spots. During a Cylent Security penetration test on a leading analytics provider, we uncovered a critical issue where a Python code execution feature—combined with a cloud misconfiguration—led to the exposure of sensitive customer data.
This case highlights how insecure design and overly permissive cloud permissions can transform a convenience feature into a high-impact breach vector.
The Vulnerability: Python Execution Meets Cloud Misconfigurations
Our assessment revealed two root causes behind the exposure:
- Unrestricted Python Environment
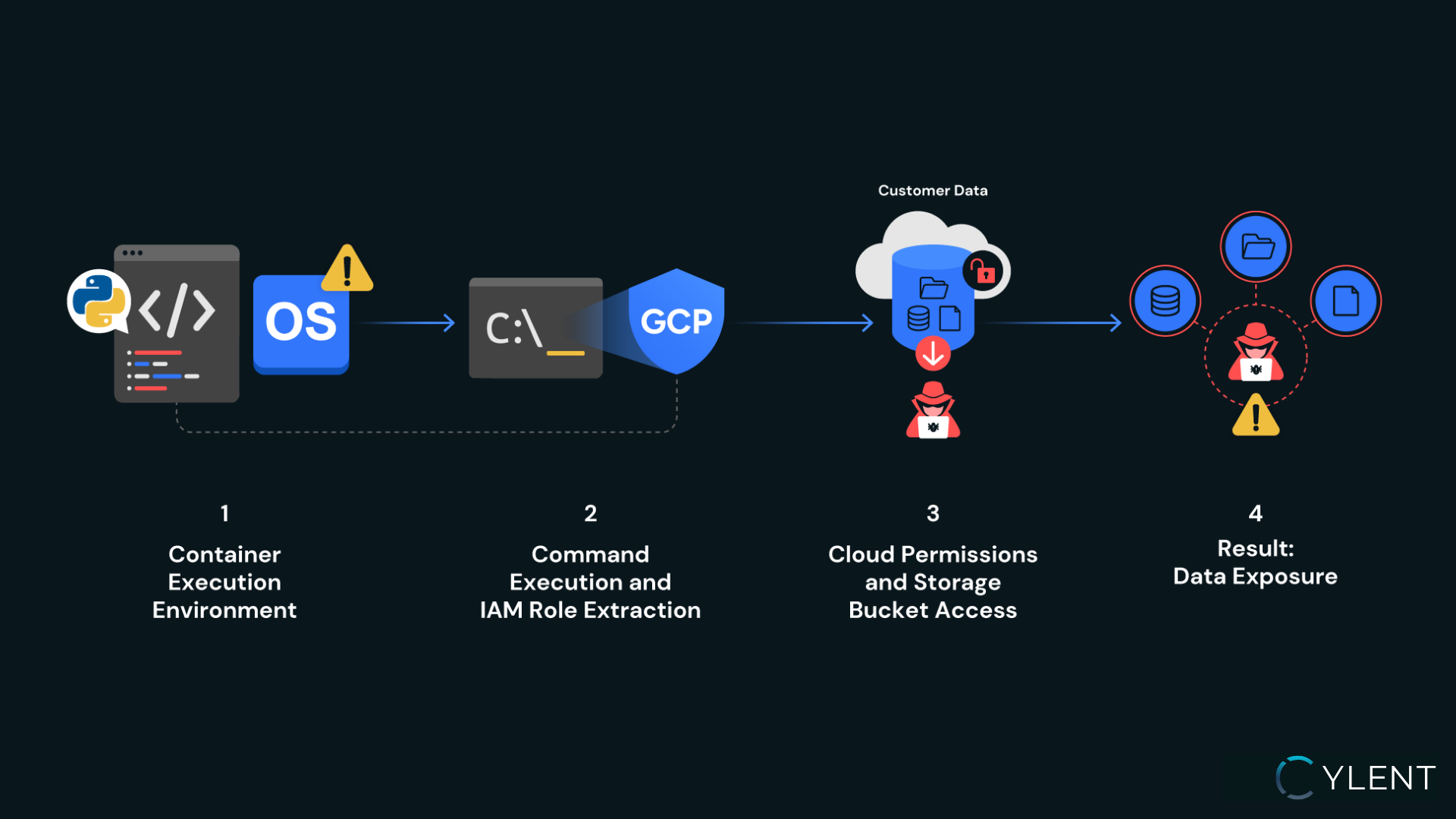
The platform allowed users to execute Python scripts in a container. While intended to be sandboxed, the environment permitted importing unrestricted libraries—including OS-level modules likeos. This meant we could run arbitrary system commands from within the container. - Overly Permissive IAM Role
The container was bound to a GCP IAM role that violated the principle of least privilege. It carried unnecessary permissions, including the ability to list and read objects in a cloud storage bucket used to store uploaded Python scripts and their execution results.
Exploit Walkthrough: From Code Execution to Data Exposure
Here’s how the attack unfolded step by step:
- Container Escape via OS Libraries
By importing theoslibrary, we executed commands directly inside the container, such as retrieving environment variables and service account details. - Credential & IAM Enumeration
Using these commands, we identified the IAM role attached to the container and enumerated its permissions. Among them was the ability to access a GCP storage bucket. - Sensitive Data Exposure
The bucket contained stored Python scripts and their output files. Some of these outputs included sensitive customer data, meaning any attacker with container access could extract private business information at scale.
How to Mitigate These Risks
Organizations building similar cloud features should adopt the following practices:
- Restrict Library Imports → enforce whitelisting of safe Python libraries. Deny OS-level access unless absolutely required.
- Enforce Least Privilege IAM → provision execution containers with scoped-down roles, limited strictly to what’s necessary.
- Audit Cloud Permissions Regularly → run recurring reviews and penetration tests to identify role misconfigurations before attackers do.
- Monitor for Abuse → implement logging and alerts for suspicious IAM role usage, particularly around sensitive storage buckets.
Secure-by-Design with Cylent Security
This case is a textbook example of how features that aren’t securely designed from day one can become liabilities. At Cylent Security, our offensive security experts help organizations:
- Threat model features like user code execution.
- Identify hidden risks in cloud and IAM configurations.
- Build secure-by-design applications that pass compliance and stand resilient against modern threats.
Build it secure. Build it Cylent.




