OAuth Oversights: Real-World Account Takeovers and How to Design Against Them

As organizations embrace OAuth2 for user authentication, design oversights in its implementation are creating new account takeover risks. While OAuth simplifies login, insecure integration can open the door to full compromise of user accounts.
In this post, we’ll cover two real-world vulnerabilities we identified during penetration tests. Both flaws allowed complete account takeover—yet both could have been prevented with a secure-by-design approach.
Vulnerability 1: Account Takeover Through Auth0 Registration Flow Overlap
Breaking Down the Attack
- Victim Registers with OAuth – A legitimate user signs up using Google OAuth, linking their Gmail.
- Attacker Registers with Email-Password – An attacker creates an account with the same Gmail address, but through the password-based flow.
- Accounts Merge Automatically – Because the application treated email as the sole identifier, it merged the two accounts, granting the attacker full control of the victim’s data and privileges.
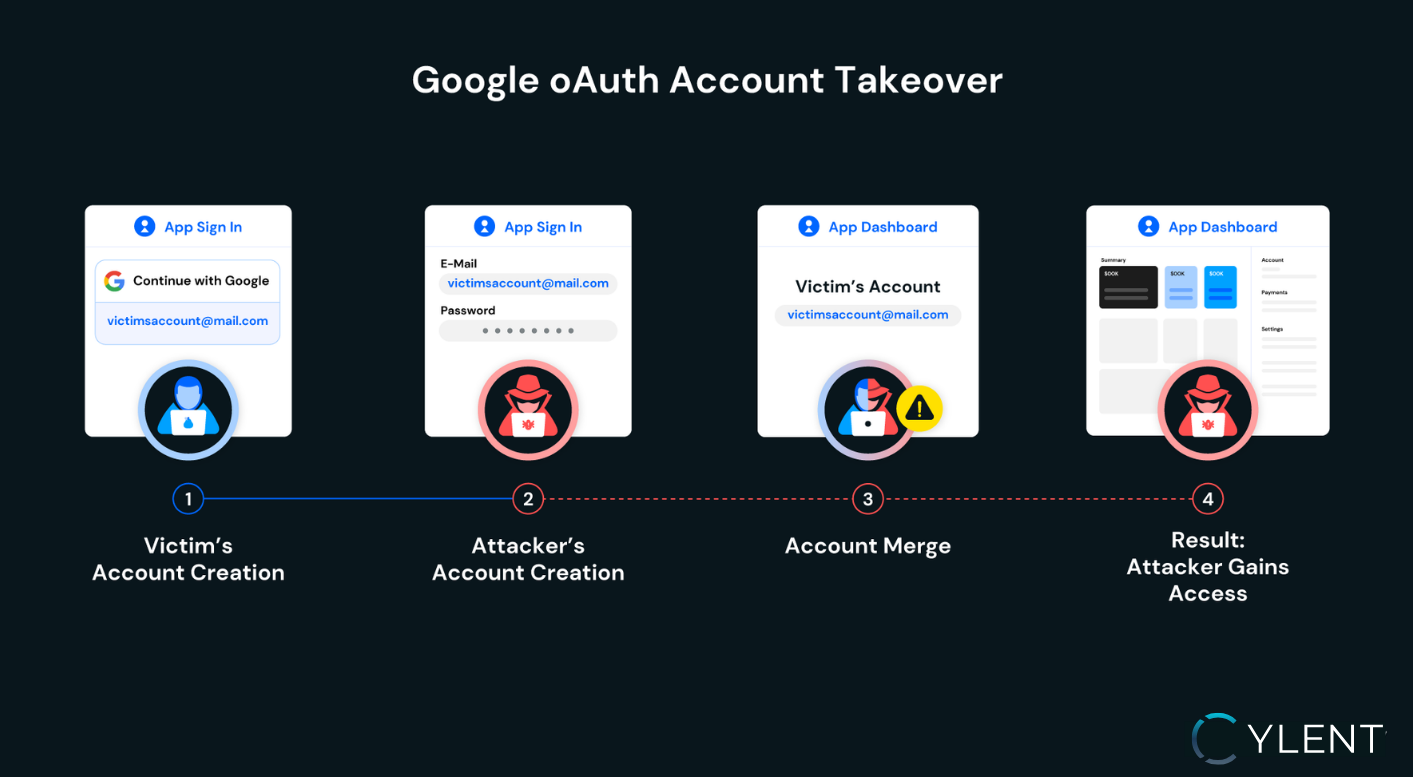
Root Cause: Weak Identity Mapping
The application assumed that email was a reliable unique identifier across all login flows. Without distinct mapping between OAuth identities and password-based identities, collisions are inevitable.
Preventive Measures
- Identity Separation: Use provider-specific IDs as unique identifiers, not just email.
- Verification Before Merge: Require additional verification (e.g., MFA) when linking accounts across methods.
Vulnerability 2: GitHub OAuth Username Collision
Exploit Scenario
- Victim Registers with Email-Password – The victim signs up with their email.
- Attacker Creates a GitHub Account – The attacker chooses a GitHub username identical to the victim’s email handle.
- Hijack via OAuth Login – When the attacker logs in with GitHub OAuth, the system incorrectly links the GitHub username to the victim’s account, resulting in takeover.
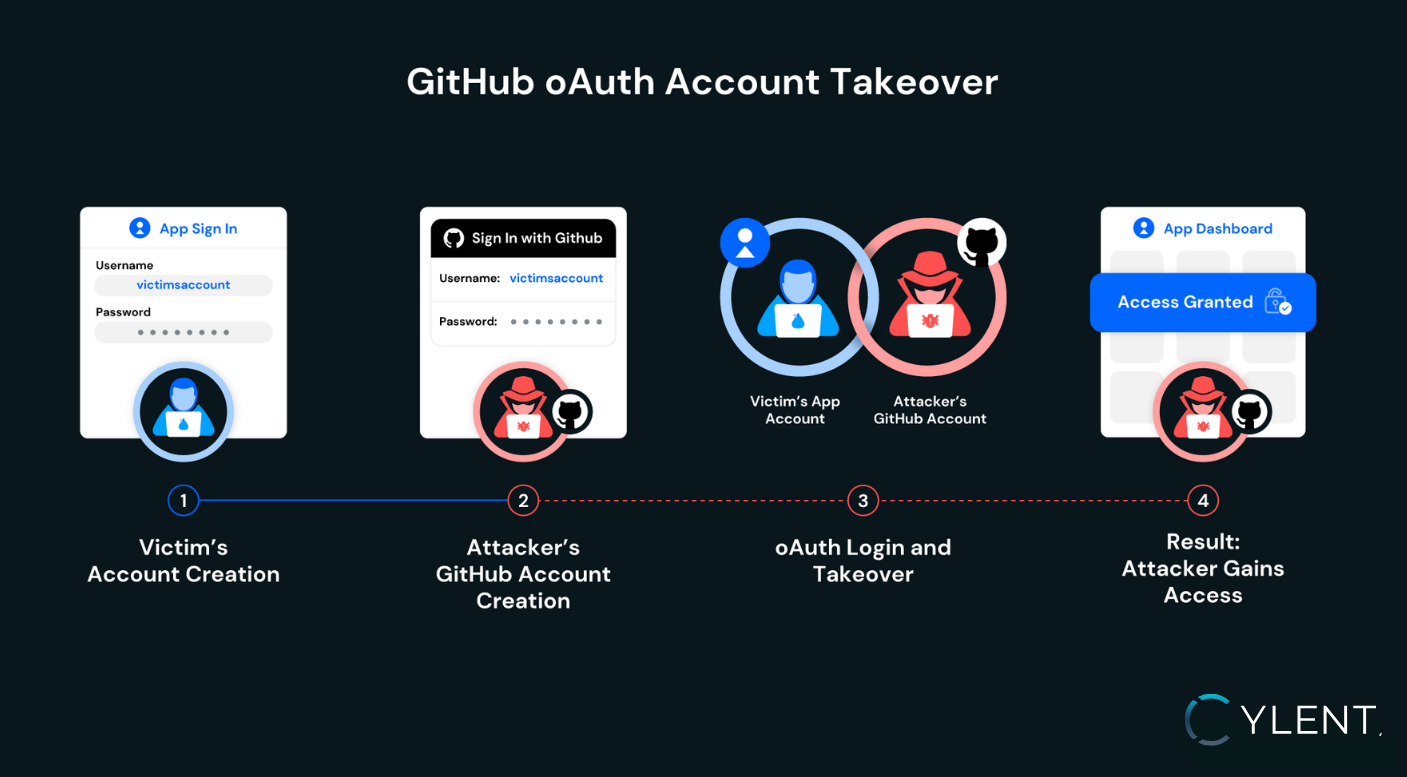
Root Cause: Insufficient Username Validation
The application allowed usernames—less unique and less secure than provider IDs—to determine account linkage.
Preventive Measures
- Robust Identity Checks: Bind accounts to identifiers unique per provider (e.g.,
subclaim in OAuth tokens). - Comprehensive Mapping Protocols: Ensure each identity source maps securely to a single user profile.
Why Secure Design Matters in OAuth and Beyond
These vulnerabilities highlight a critical truth: account security isn’t just about strong authentication—it’s about secure design at the architecture level.
Without secure-by-design principles, simple oversights can lead to catastrophic account takeovers, compliance failures, and reputational damage.
Cylent Security: Secure by Design
At Cylent Security, we help organizations prevent vulnerabilities like these before they reach production. Through threat modeling, secure design reviews, and rigorous penetration testing, we ensure your applications are resilient from the ground up.
Don’t wait until attackers find the gap. Your authentication flow may already be vulnerable. Contact us to design it secure from day one.




